Encryption Systems
Encryption Systems provide a secure, data protection system for online shopping all over the world instantly! As in many new industries to the Internet, it became a necessity for purchasers to continue shopping "online" over the Internet - or the entire system would come to a standstill if hackers could constantly intercept personal data.
Initially, when people would communicate online, there were no safeguards in place to protect data. Even now, people send emails especially without any type of "protection" of their data. Perhaps someday, we will be able to send and receive encryption emails. Of course, BOTH parties must use an encryption service email system for it to work - always remember that!
Just as a side note - please do NOT send credit card information, expiration dates and the security code over emails.
They are NOT SECURE!!
The way encryption works is basically all the information is coded in such a way that it can't be easily seen, read or found online. It also requires the receiving end of a data transmission to provide a code that is exact and particular to each message it receives.
The encryption system is now on a third generation of a coding process that must be read and interpreted on each end. Unfortunately, all this data is traveling literally all over the world. This provides hackers an opportunity to intercept and "read" data while on it's way throughout the Internet.
As per Wikipedia:
"In cryptography, encryption is the process of encoding messages (or information) in such a way that eavesdroppers or hackers cannot read it, but that authorized parties can.[1]:374 In an encryption scheme, the message or information (referred to as plaintext) is encrypted using an encryption algorithm, turning it into an unreadable ciphertext (ibid.). This is usually done with the use of an encryption key, which specifies how the message is to be encoded. Any adversary that can see the ciphertext should not be able to determine anything about the original message. An authorized party, however, is able to decode the ciphertext using a decryption algorithm, that usually requires a secret decryption key, that adversaries do not have access to. For technical reasons, an encryption scheme usually needs a key-generation algorithm to randomly produce keys."
Fortunately, the methods being used today are getting really good at protecting personal, corporate and military data.
There are 3 versions of encryption systems in use today.
The first is just a basic system that adds a "s" to the http of a URL that will be used to transmit information. For today's standards - this is not really secure - too easy to hack into it as it travels through the Internet.
The second system illustrates the same "s" at the end of the http of a URL. However, this system will show a Grey "closed lock" up on the beginning of the URL in the browser line of your browser. This version means the website has enabled a secure system - but does NOT verify the Website's OWNER.
The third and most secure will be the same in appearance - but the lock and the company that is guaranteeing the encryption will be displayed in GREEN. The means that the website is secure, using a modern encryption AND the Website OWNER has been VERIFIED!!! Much more SECURE!!!!
Green Encryption Example
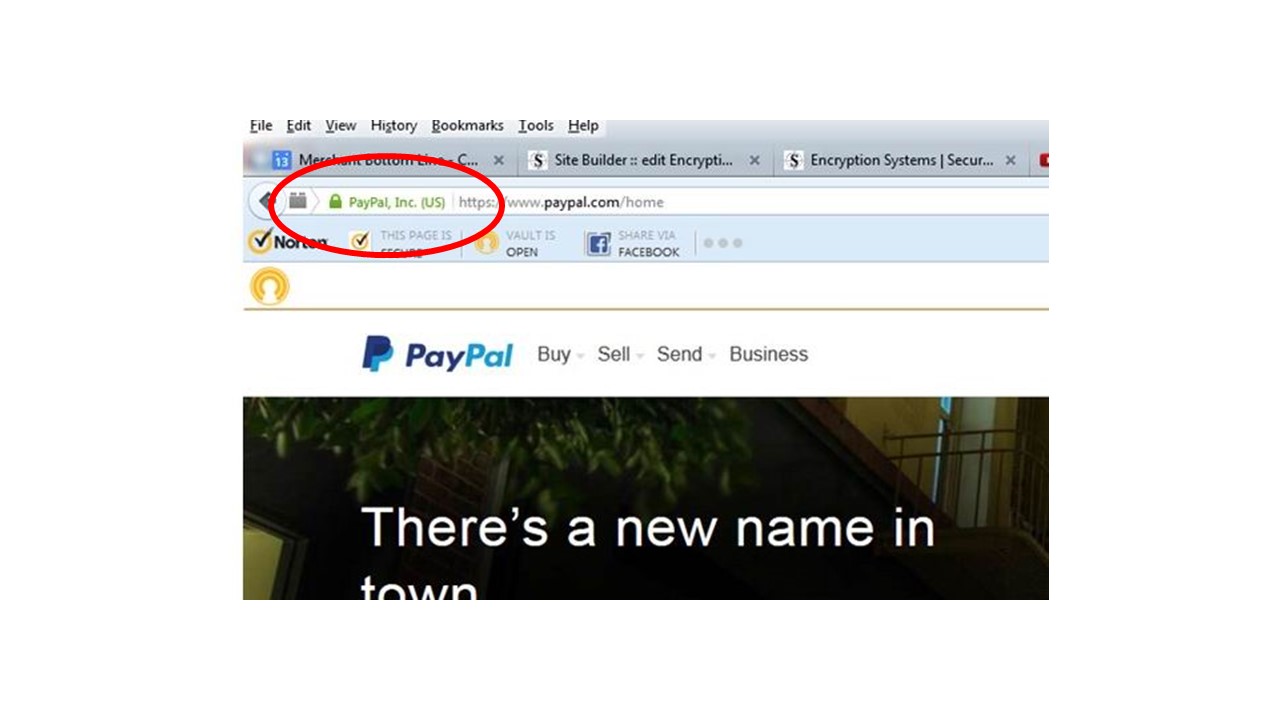
The picture above illustrates a Green Padlock AND the name of the Website as VERIFIED - Green Also.
A "website" can't just add that "s" to its URL. They must legally purchase a "Certificate" from an accredited vendor that is strictly for this purpose. It is only meaningful when it is transmitting information to another "s" URL page.
The "degrees" of SSL Security (s) on the URL address will depend on the mathematical number of "possibilities" that are used to decode a message.
The latest version of encryption systems will use a 256 digit mathematical code to protect the information - on both ends of the transmission! Very secure, indeed!
This most secure system uses the latest technology to protect the data and has it very well encoded and as hack free as possible. This system will use a special key to encode the transmission before it even starts and only the end receiver has the duplicate key to read the final transmission. As in all systems on the Internet, people will be always trying to capture data illegally. This will continue as long as we have the Internet - which doesn't seem to be going away!! A great source to understand this easily is Rapid SSL - an actual reseller of these very special certificates.
A secure Gateway System Provider, such as Authorize.Net or First Data Clover provides an excellent source of credit card processing over the Internet with the latest very secure Encryption technology in place.
Please Contact Us if you have any questions or concerns.
Questions? Or need help?? Contact Me






